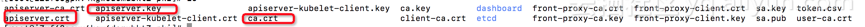
首先,如果是普通版kubernetes集群,可以登陆到master集群,可以使用私钥证书的方式访问。证书路径:master的/etc/kubernetes/pki 下面。
![888e86f4dd592d347db5555f34f7aa9edb422c30]()
使用命令:
curl --cacert ca.crt --cert apiserver.crt --key apiserver.key https://$server/api
server是apiserver公网访问地址
curl --cacert ca.crt --cert apiserver.crt --key apiserver.key https://server:6443/api
{
"kind": "APIVersions",
"versions": [
"v1"
],
"serverAddressByClientCIDRs": [
{
"clientCIDR": "0.0.0.0/0",
"serverAddress": "192.168.0.251:6443"
}
]
}
接下来介绍一下使用ServiceAccount Token的方式访问集群。serviceaccount的权限由集群中对应的rolebinding决定,官方文档 https://kubernetes.io/docs/reference/access-authn-authz/rbac/
请选择对应权限的ServiceAccount来获取token,我这边选择的是admin ServiceAccount
kubectl get sa admin -n kube-system -o yaml
apiVersion: v1
kind: ServiceAccount
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"v1","kind":"ServiceAccount","metadata":{"annotations":{},"name":"admin","namespace":"kube-system"}}
creationTimestamp: 2018-11-05T09:23:39Z
name: admin
namespace: kube-system
resourceVersion: "889"
selfLink: /api/v1/namespaces/kube-system/serviceaccounts/admin
uid: 7af4f177-e0dc-11e8-8ef4-00163e009d2a
secrets:
- name: admin-token-5tctj
查看对应的clusterrolebinding:
kubectl get clusterrolebinding admin -oyaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"rbac.authorization.k8s.io/v1beta1","kind":"ClusterRoleBinding","metadata":{"annotations":{},"name":"admin","namespace":""},"roleRef":{"apiGroup":"rbac.authorization.k8s.io","kind":"ClusterRole","name":"cluster-admin"},"subjects":[{"kind":"ServiceAccount","name":"admin","namespace":"kube-system"}]}
creationTimestamp: 2018-11-05T09:23:39Z
name: admin
resourceVersion: "886"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterrolebindings/admin
uid: 7af6ff9d-e0dc-11e8-8ef4-00163e009d2a
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cluster-admin
subjects:
- kind: ServiceAccount
name: admin
namespace: kube-system
查看admin sa绑定的clusterrole和对应的权限。命令:
kubectl get clusterrole cluster-admin -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
annotations:
rbac.authorization.kubernetes.io/autoupdate: "true"
creationTimestamp: 2018-11-05T09:18:49Z
labels:
kubernetes.io/bootstrapping: rbac-defaults
name: cluster-admin
resourceVersion: "38"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/cluster-admin
uid: ce28c0e7-e0db-11e8-9852-00163e009d2a
rules:
- apiGroups:
- '*'
resources:
- '*'
verbs:
- '*'
- nonResourceURLs:
- '*'
verbs:
- '*'
获取对应sa的secret从中获取token。并进行base64解码。
kubectl get secret admin-token-5tctj -n kube-system -o jsonpath={".data.token"} | base64 -d
eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi01dGN0aiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhZjRmMTc3LWUwZGMtMTFlOC04ZWY0LTAwMTYzZTAwOWQyYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.aMzef7qssxhFCkKHYFX99XBCkA_lnpKQhBvWPJ_AEsg89HUJ9cgYs2M7VRQJ2KcsG1BndSW0Ne-yLdsXFGDMaIRF58Rz02V99ViqAH8W86UZqcgARlw6DbYtpyHx2LZp4_HbrOy0xHJXGOx0FzwbCNJR5TE5LAZWx2Q5WowuxzdIhpkr15tn9UTZB0i2VXyANG3D6xyf1M67ojav59eC04qWu3ZuFC2GgngHGbZ1qnP55UnFTHWdFtHAzU5qAX7jrWJAOBdSPXwoxC9XTIBoL2umQk2XQN-OsBnQ_saXXLPe2cdpKdoboJCZgcUfO-5D94KO-5P8wNVhGWubNutvug
最后使用该token访问apiserver:
最后使用公网slb地址访问。curl -k -H 'Authorization: Bearer token' https://111.111.111.111:6443
例如:
curl -k -H 'Authorization: Bearer eyJhbGciOiJSUzI1NiIsImtpZCI6IiJ9.eyJpc3MiOiJrdWJlcm5ldGVzL3NlcnZpY2VhY2NvdW50Iiwia3ViZXJuZXRlcy5pby9zZXJ2aWNlYWNjb3VudC9uYW1lc3BhY2UiOiJrdWJlLXN5c3RlbSIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VjcmV0Lm5hbWUiOiJhZG1pbi10b2tlbi01dGN0aiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50Lm5hbWUiOiJhZG1pbiIsImt1YmVybmV0ZXMuaW8vc2VydmljZWFjY291bnQvc2VydmljZS1hY2NvdW50LnVpZCI6IjdhZjRmMTc3LWUwZGMtMTFlOC04ZWY0LTAwMTYzZTAwOWQyYSIsInN1YiI6InN5c3RlbTpzZXJ2aWNlYWNjb3VudDprdWJlLXN5c3RlbTphZG1pbiJ9.aMzef7qssxhFCkKHYFX99XBCkA_lnpKQhBvWPJ_AEsg89HUJ9cgYs2M7VRQJ2KcsG1BndSW0Ne-yLdsXFGDMaIRF58Rz02V99ViqAH8W86UZqcgARlw6DbYtpyHx2LZp4_HbrOy0xHJXGOx0FzwbCNJR5TE5LAZWx2Q5WowuxzdIhpkr15tn9UTZB0i2VXyANG3D6xyf1M67ojav59eC04qWu3ZuFC2GgngHGbZ1qnP55UnFTHWdFtHAzU5qAX7jrWJAOBdSPXwoxC9XTIBoL2umQk2XQN-OsBnQ_saXXLPe2cdpKdoboJCZgcUfO-5D94KO-5P8wNVhGWubNutvug' https://111.111.111.111:6443/api
{
"kind": "APIVersions",
"versions": [
"v1"
],
"serverAddressByClientCIDRs": [
{
"clientCIDR": "0.0.0.0/0",
"serverAddress": "192.168.0.252:6443"
}
]
}