阿里云容器服务Kubernetes用户授权管理分为2个级别:一个是RAM访问控制,即设定用户对k8s集群的访问权限,比如查看集群列表,创建/删除集群的权限,是否能够对集群进行扩容等等;另一个是需要在集群内对用户进行细粒度的授权,比如是否允许用户部署应用,以及对集群内资源的修改删除。本文将对这两个部分进行简单介绍,从而掌握对集群的正确授权管理,特别演示了如何单独创建集群用户并为其授权的过程。
Kubernetes 阿里云容器服务RAM访问控制
在RAM访问控制里面,有2个系统策略:AliyunCSFullAccess和AliyunCSReadOnlyAccess。很明显前者是具有对k8s集群的完全访问控制,能够在阿里云控制台创建删除集群。而后这只读权限的内容是"cs:Get",也就是说只具有Get权限。这两个系统策略的颗粒度是比较大的,要想精细化权限管理,需要进行自定义策略并赋给指定用户。下表是所有集群具有的操作(参考自定义 RAM 授权策略):
| Action |
说明 |
| CreateCluster |
创建集群 |
| AttachInstances |
向集群中添加已有 ECS 实例 |
| ScaleCluster |
扩容集群 |
| GetClusters |
查看集群列表 |
| GetClusterById |
查看集群详情 |
| ModifyClusterName |
修改集群名称 |
| DeleteCluster |
删除集群 |
| UpgradeClusterAgent |
升级集群 Agent |
| GetClusterLogs |
查看集群的操作日志 |
| GetClusterEndpoint |
查看集群接入点地址 |
| GetClusterCerts |
下载集群证书 |
| RevokeClusterCerts |
吊销集群证书 |
| BindSLB |
为集群绑定负载均衡实例 |
| UnBindSLB |
为集群解绑负载均衡实例 |
| ReBindSecurityGroup |
为集群重新绑定安全组 |
| CheckSecurityGroup |
检测集群现有的安全组规则 |
| FixSecurityGroup |
修复集群的安全组规则 |
| ResetClusterNode |
重置集群中的节点 |
| DeleteClusterNode |
移除集群中的节点 |
| GetClusterProjects |
查看集群下的应用 |
| CreateTriggerHook |
为应用创建触发器 |
| GetTriggerHook |
查看应用的触发器列表 |
| RevokeTriggerHook |
删除应用的触发器 |
| CreateClusterToken |
创建 Token |
| UpdateClusterTags |
编辑集群标签 |
阿里云环境如何用子账号对用户进行授权
![1_cluster 1_cluster]()
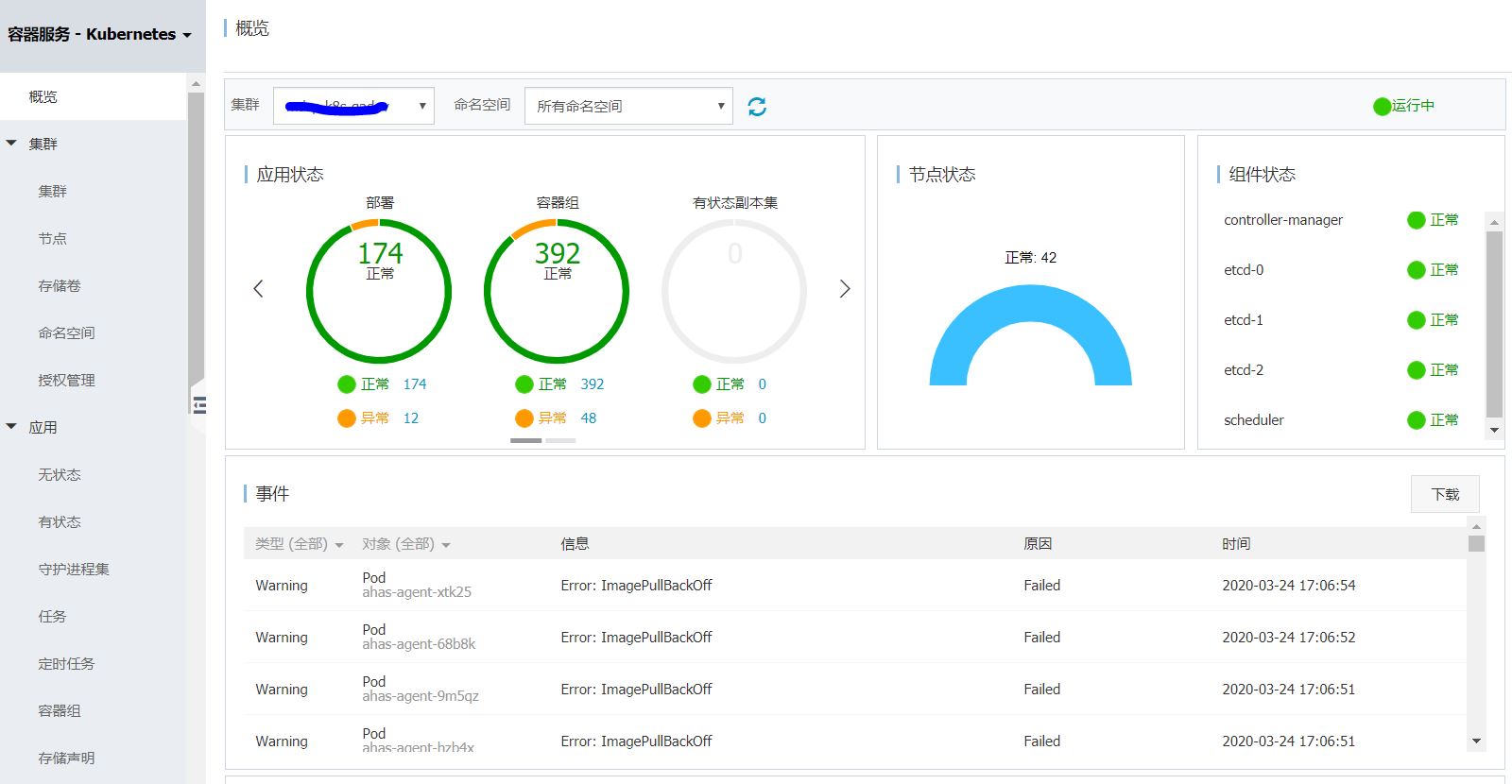
具有阿里云RAM权限只是具有管理阿里云集群的第一步,要进行集群的使用和运维,还需要利用Kubernetes RBAC进行单独的访问控制。
![1_accesscontrolrbac 1_accesscontrolrbac]()
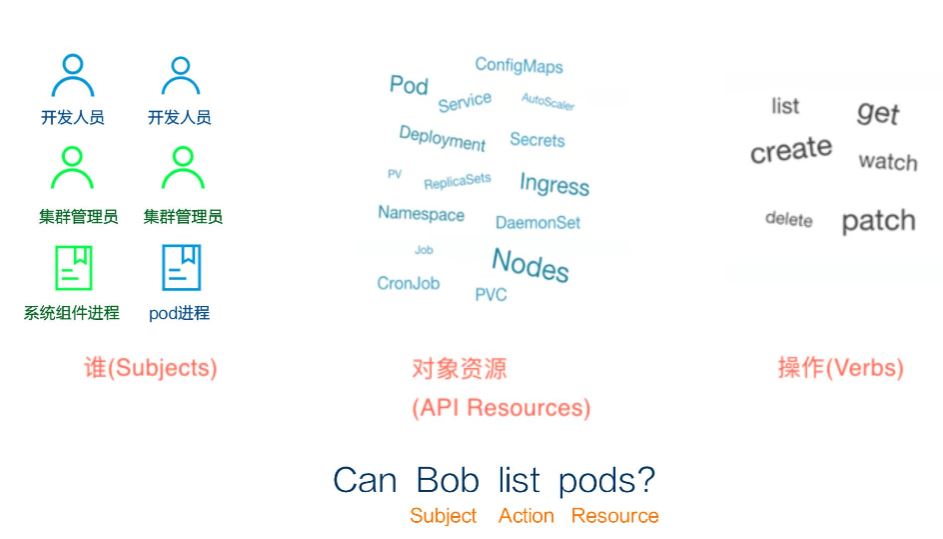
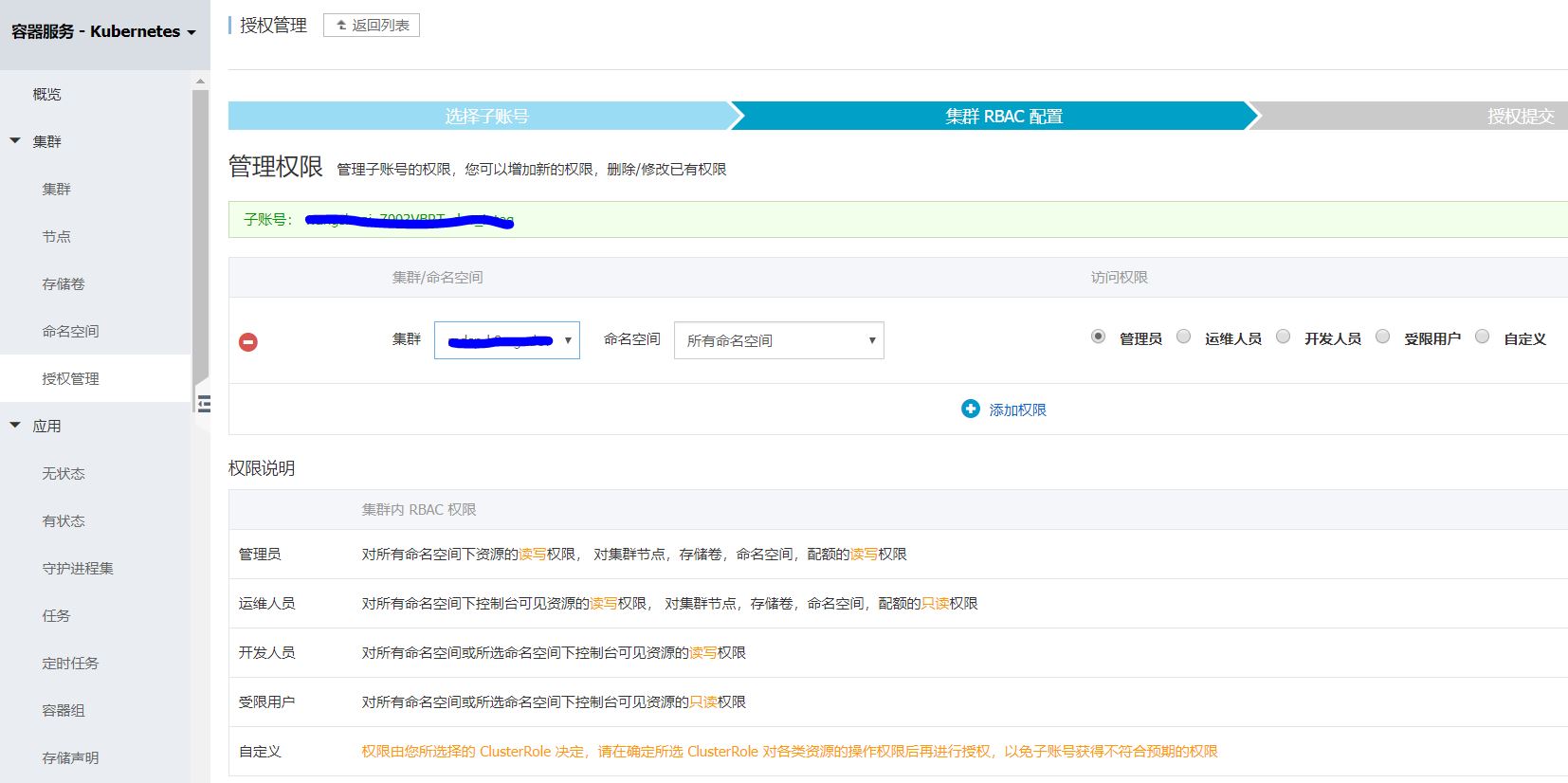
其实这个跟阿里云的RAM访问控制Policy比较类似,就是描述谁可以对K8S的资源进行什么样的操作。不同的策略赋给不同的用户,阿里云预置的一组策略可以关联于角色Role,然后在阿里云集群授权中就可以将相应的Role赋给具体某一用户。这里面看到的管理员,运维人员,开发人员等其实就是不同的角色,后面我们可以看到他们对应的具体Policy。
![2_shouquanguanli 2_shouquanguanli]()
![3_shouquanguanli 3_shouquanguanli]()
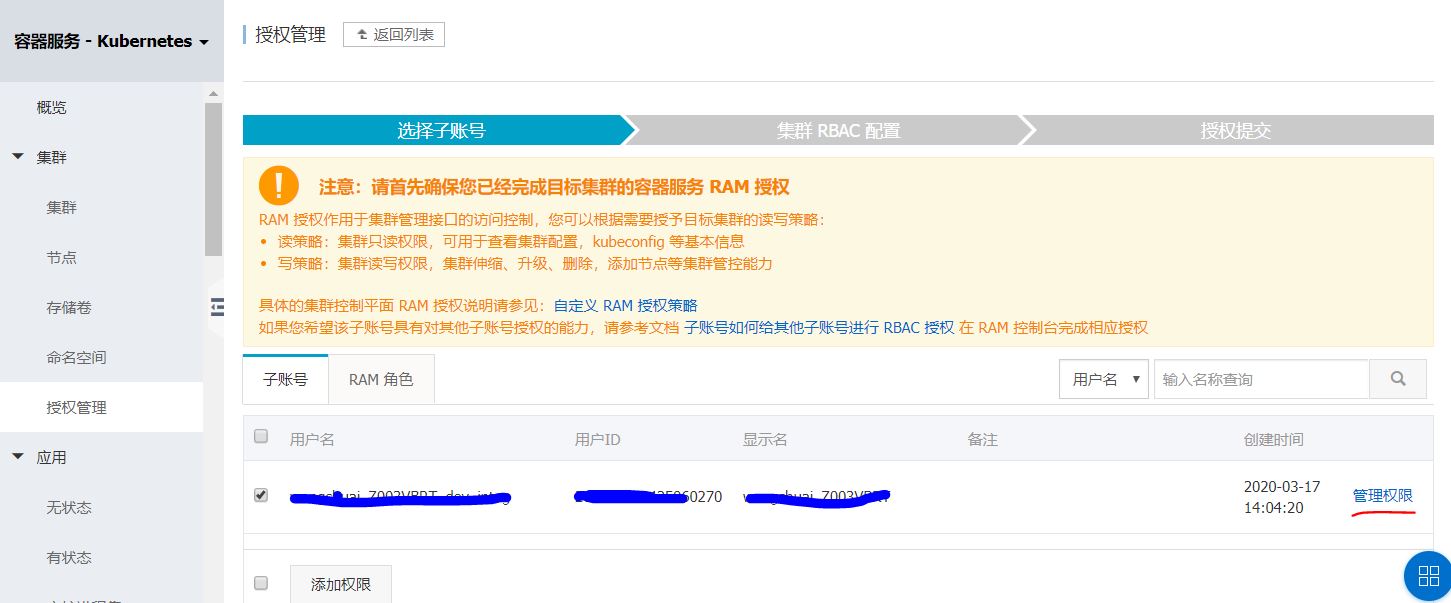
阿里云主账号具有最大的管理权限,可以做集群的授权操作,但一般我们不建议用主账号做太多的操作,所以尽量用管理员账户操作就可以了。但对于K8S授权,即使是系统管理员,在对集群做授权时,也会提示“当前子账号不具备授权管理权限,请联系主帐号或权限管理员授权。”,这是因为K8S授权需要先用主账号对集群的管理员先赋予集群管理员角色,这样这个管理员才能对其它子账号进行授权操作。准确地说,授权需要满足2个条件,一个是RAM访问控制读权限(参考link),另一个是集群中对apiGroups的rbac.authorization.k8s.io的访问权限。
Kubernetes RBAC(Role Based Access Control)基于角色的访问控制
我们用下面的命令可以查看K8S中的ClusterRole,ClusterRoleBinding。
# kubectl get ClusterRole
NAME AGE
admin 1y
ahas 245d
alibaba-log-controller 1y
alicloud-disk-controller-runner 1y
arms-pilot-ack-arms-pilot-role 200d
cluster-admin 1y
cs:admin 340d
cs:dev 340d
cs:heapster 1y
cs:ns:dev 1y
cs:ops 337d
cs:restricted 340d
deployment-reader 1y
drain-node 109d
edit 1y
flannel 1y
kube-state-metrics 1y
nginx-ingress-controller 320d
pod-reader 1y
system:aggregate-to-admin 1y
system:aggregate-to-edit 1y
system:aggregate-to-view 1y
system:auth-delegator 1y
system:aws-cloud-provider 1y
system:basic-user 1y
system:certificates.k8s.io:certificatesigningrequests:nodeclient 1y
system:certificates.k8s.io:certificatesigningrequests:selfnodeclient 1y
system:cloud-controller-manager 1y
system:controller:attachdetach-controller 1y
system:controller:certificate-controller 1y
system:controller:clusterrole-aggregation-controller 1y
system:controller:cronjob-controller 1y
system:controller:daemon-set-controller 1y
system:controller:deployment-controller 1y
system:controller:disruption-controller 1y
system:controller:endpoint-controller 1y
system:controller:expand-controller 1y
system:controller:generic-garbage-collector 1y
system:controller:horizontal-pod-autoscaler 1y
system:controller:job-controller 1y
system:controller:namespace-controller 1y
system:controller:node-controller 1y
system:controller:persistent-volume-binder 1y
system:controller:pod-garbage-collector 1y
system:controller:pv-protection-controller 1y
system:controller:pvc-protection-controller 1y
system:controller:replicaset-controller 1y
system:controller:replication-controller 1y
system:controller:resourcequota-controller 1y
system:controller:route-controller 1y
system:controller:service-account-controller 1y
system:controller:service-controller 1y
system:controller:statefulset-controller 1y
system:controller:ttl-controller 1y
system:coredns 1y
system:csi-external-attacher 1y
system:csi-external-provisioner 1y
system:discovery 1y
system:heapster 1y
system:kube-aggregator 1y
system:kube-controller-manager 1y
system:kube-dns 1y
system:kube-scheduler 1y
system:kubelet-api-admin 1y
system:node 1y
system:node-bootstrapper 1y
system:node-problem-detector 1y
system:node-proxier 1y
system:persistent-volume-provisioner 1y
system:volume-scheduler 1y
test-role 2h
view 1y
查看ClusterRoleBinding:
# kubectl get clusterrolebinding
NAME AGE
202729146928739501-clusterrolebinding 218d
202865947013061057-clusterrolebinding 336d
203542248038995370-clusterrolebinding 333d
204696546927216725-clusterrolebinding 1d
admin 1y
ahas 245d
alibaba-log-controller 1y
aliyun-acr-credential-helper-rolebinding 1y
arms-pilot-ack-arms-pilot-role-binding 200d
cluster-admin 1y
deployment-reader 1y
drain-node 109d
flannel 1y
global-job-controller-role-binding 329d
kube-state-metrics 1y
kubeadm:kubelet-bootstrap 1y
kubeadm:node-autoapprove-bootstrap 1y
kubeadm:node-autoapprove-certificate-rotation 1y
kubeadm:node-proxier 1y
nginx-ingress-controller-starterservices-dev 224d
nginx-ingress-controller-starterservices-gadev 320d
node-masters-role-binding 329d
pod-reader 1y
run-alicloud-disk-controller 1y
system:aws-cloud-provider 1y
system:basic-user 1y
system:cloud-controller-manager 1y
system:cloud-node-controller 1y
system:controller:attachdetach-controller 1y
system:controller:certificate-controller 1y
system:controller:clusterrole-aggregation-controller 1y
system:controller:cronjob-controller 1y
system:controller:daemon-set-controller 1y
system:controller:deployment-controller 1y
system:controller:disruption-controller 1y
system:controller:endpoint-controller 1y
system:controller:expand-controller 1y
system:controller:generic-garbage-collector 1y
system:controller:horizontal-pod-autoscaler 1y
system:controller:job-controller 1y
system:controller:namespace-controller 1y
system:controller:node-controller 1y
system:controller:persistent-volume-binder 1y
system:controller:pod-garbage-collector 1y
system:controller:pv-protection-controller 1y
system:controller:pvc-protection-controller 1y
system:controller:replicaset-controller 1y
system:controller:replication-controller 1y
system:controller:resourcequota-controller 1y
system:controller:route-controller 1y
system:controller:service-account-controller 1y
system:controller:service-controller 1y
system:controller:statefulset-controller 1y
system:controller:ttl-controller 1y
system:coredns 1y
system:discovery 1y
system:kube-controller-manager 1y
system:kube-dns 1y
system:kube-scheduler 1y
system:node 1y
system:node-proxier 1y
system:pvl-controller 1y
system:route-controller 1y
system:shared-informers 1y
system:volume-scheduler 1y
test-rolebinding 2h
tiller-cluster-rule 1y
cs:admin, cs:ops, cs:dev, cs:restricted分别代表阿里云预置的4个角色:管理员,运维人员,开发人员,受限用户,它们的权限依次递减,其中受限用户只对部分资源具有读权限。
我们查看其中的一个ClusterRoleBinding, ID为202729146928739501用户赋予了cs:ops的角色。
# kubectl get clusterrolebinding/202729146928739501-clusterrolebinding -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
creationTimestamp: 2019-08-19T05:22:03Z
name: 202729146928739501-clusterrolebinding
resourceVersion: "111811902"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterrolebindings/202729146928739501-clusterrolebinding
uid: 46ec07c5-c241-11e9-b90f-00163e00519d
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: cs:ops
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: "202729146928739501"
接下来就可以继续查看cs:ops到底具有什么样的权限:
# kubectl get clusterrole/cs:ops -o yaml
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
creationTimestamp: 2019-04-22T07:57:30Z
name: cs:ops
resourceVersion: "47812320"
selfLink: /apis/rbac.authorization.k8s.io/v1/clusterroles/cs%3Aops
uid: 472ef445-64d4-11e9-bb7e-00163e06e73f
rules:
- apiGroups:
- ""
resources:
- pods
- pods/attach
- pods/exec
- pods/portforward
- pods/proxy
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- persistentvolumeclaims
- replicationcontrollers
- replicationcontrollers/scale
- secrets
- serviceaccounts
- services
- services/proxy
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- ""
resources:
- bindings
- events
- limitranges
- namespaces/status
- replicationcontrollers/status
- pods/log
- pods/status
- resourcequotas
- resourcequotas/status
- componentstatuses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- namespaces
- nodes
- persistentvolumes
verbs:
- get
- list
- watch
- patch
- apiGroups:
- apps
resources:
- daemonsets
- deployments
- deployments/rollback
- deployments/scale
- replicasets
- replicasets/scale
- statefulsets
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- autoscaling
resources:
- horizontalpodautoscalers
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- batch
resources:
- cronjobs
- jobs
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- extensions
resources:
- daemonsets
- deployments
- deployments/rollback
- deployments/scale
- ingresses
- replicasets
- replicasets/scale
- replicationcontrollers/scale
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
- apiGroups:
- servicecatalog.k8s.io
resources:
- clusterserviceclasses
- clusterserviceplans
- clusterservicebrokers
- serviceinstances
- servicebindings
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- servicecatalog.k8s.io
resources:
- clusterservicebrokers/status
- clusterserviceclasses/status
- clusterserviceplans/status
- serviceinstances/status
- serviceinstances/reference
- servicebindings/status
verbs:
- update
- apiGroups:
- storage.k8s.io
resources:
- storageclasses
verbs:
- get
- list
- watch
- apiGroups:
- alicloud.com
resources:
- '*'
verbs:
- create
- delete
- get
- list
- patch
- update
- watch
- apiGroups:
- policy
resources:
- poddisruptionbudgets
verbs:
- create
- delete
- deletecollection
- get
- list
- patch
- update
- watch
阿里云授权页面中的自定义就是可以选取集群中已经存在的一些角色,当然也可以创建自己的权限和角色,然后分配给指定的用户。
如何为Kubernetes创建一个独立于阿里云的用户并进行授权
除了在阿里云容器服务控制台中对阿里云用户进行授权外,集群管理者也可以单独创建一个用户并对其进行授权,这样就可以给一个没有阿里云账户的用户通过api或者kubectl命令来使用和管理集群。以下的步骤举例说明如何创建用户bob,并给bob授权,以及bob如何配置使用。
创建用户
登陆到master节点
# cd /etc/kubernetes/pki
创建bob 私钥
# openssl genrsa -out bob.key 2048
创建bob CSR,并将bob分配到test这个组中。
# openssl req -new -key bob.key -out bob.csr -subj "/CN=bob/O=test"
通过集群CA签发bob证书。管理员将证书文件和bob的私钥一起发给bob用户。
# openssl x509 -req -in bob.csr -CA ca.pem -CAkey ca-key.pem -CAcreateserial -out bob.crt -days 365
上面在创建bob CSR的时候/CN=bob代表用户名,/O=test代表用户所在的组。system:masters是系统组,如果选择这个组,用户缺省就具有了cluster admin的权限。
bob如何配置使用证书
bob得到CA签发的证书和私钥后,首先需要下载kubectl,然后通过下面命令配置.kube/config文件。
#添加集群连接信息。包括CA证书。
C:\Users\mdw3sr\Desktop>kubectl config set-cluster sandbox --certificate-authority=ca.crt --embed-certs=true --server=https://<K8S集群公网IP>:6443
Cluster "sandbox" set.
#将bob密钥信息加入配置中
C:\Users\mdw3sr\Desktop>kubectl config set-credentials bob --client-certificate=bob.crt --client-key=bob.key --embed-certs=true
User "bob" set.
#将新的context入口加入配置中
C:\Users\mdw3sr\Desktop>kubectl config set-context bob --cluster=sandbox --user=bob
Context "kubernetes" created.
#使用bob context
C:\Users\mdw3sr\Desktop>kubectl config use-context bob
Switched to context "bob".
这样运行kubectl cluster-info就能看到集群信息了,虽然还有些信息因为权限问题不能正确显示。
C:\Users\mdw3sr\Desktop>kubectl cluster-info
Kubernetes master is running at https://106.15.157.9:6443
To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.
Error from server (Forbidden): services is forbidden: User "bob" cannot list resource "services" in API group "" in the namespace "kube-system"
C:\Users\mdw3sr\Desktop>kubectl get pod
No resources found.
Error from server (Forbidden): pods is forbidden: User "bob" cannot list resource "pods" in API group "" in the namespace "default"
为用户bob设置权限
从上面结果可以看出,如果没有设置任何权限,bob在集群内是没有任何资源访问能力,所以管理员需要对bob进行集群内授权。
为bob创建ClusterRole和ClusterRoleBinding
# cat > test.yaml <<EOF
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
name: test-role
rules:
- apiGroups: [""]
resources: ["pods","services"]
verbs: ["get", "list"]
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
name: test-rolebinding
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: test-role
subjects:
- apiGroup: rbac.authorization.k8s.io
kind: User
name: bob
EOF
# kubectl apply -f test.yaml
clusterrole.rbac.authorization.k8s.io/test-role created
clusterrolebinding.rbac.authorization.k8s.io/test-rolebinding created
然后,bob这边再测试之前的命令,就可以正确执行了。结果如下:
C:\Users\mdw3sr\Desktop>kubectl cluster-info
Kubernetes master is running at https://106.10.157.9:6443
Heapster is running at https://106.10.157.9:6443/api/v1/namespaces/kube-system/services/heapster/proxy
KubeDNS is running at https://106.10.157.9:6443/api/v1/namespaces/kube-system/services/kube-dns:dns/proxy
monitoring-influxdb is running at https://106.10.157.9:6443/api/v1/namespaces/kube-system/services/monitoring-influxdb/proxy
To further debug and diagnose cluster problems, use 'kubectl cluster-info dump'.
C:\Users\mdw3sr\Desktop>kubectl get pod
NAME READY STATUS RESTARTS AGE
nginx-deployment-bb54749c-426cb 1/1 Running 0 104d
nginx-deployment-bb54749c-qcvc5 1/1 Running 0 104d
nginx-v1-5bc8bf76db-7rnkf 1/1 Running 1 230d
nginx-v1-5bc8bf76db-r7k5r 1/1 Running 0 185d
patch-demo-7f54465dd5-jhr5c 2/2 Running 0 29d
patch-demo-7f54465dd5-w5hx2 2/2 Running 0 29d
# 因为并没有赋给bob 获取namespace的权限,所以bob仍然不能访问namespace信息。
C:\Users\mdw3sr\Desktop>kubectl get ns
No resources found.
Error from server (Forbidden): namespaces is forbidden: User "bob" cannot list resource "namespaces" in API group "" at the cluster scope
大家也可以通过对bob设置不同的权限来学习验证具体的行为。